Do you know what quantum key distribution is? We tell you. Cybersecurity seems to have found in quantum technology the perfect ally to face the most skillful Cyber attacks.
Every time you send an email, indicate your bank details in a purchase or subscribe to an online service, all these data depend on the strength of Cybersecurity systems so as not to end up in the wrong hands.
Whether it is the personal data of a user on the Internet or the confidential documents of companies and governments, everything is susceptible to a computer attack. Therefore, this information is protected by encryption systems such as asymmetric RSA, whose key is the product of two very long prime numbers.
The problem is that the more advanced machines or the new quantum computers, as they evolve, seem more capable of solving those keys in a matter of minutes, nullifying the entire RSA security system that is one of the bases of the internet. Before that situation arrives, the researchers work on a solution based on quantum physics.
Quantum key distribution is a cryptographic key distribution technique protected by the properties of quantum mechanics. These principles determine that the polarization of photons, the smallest unit of energy in a light wave and that they cannot be divided, have the quantum quality of vibrating in two perpendicular directions at the same time.
We can have photons polarized in one of two reference directions perpendicular to each other (vertical or horizontal), or in a superposition of the two directions at the same time (vertical AND horizontal at the same time). If, when measuring the polarization of the photon, it coincides with one of the two directions chosen as a reference, we obtain the correct measurement (vertical or horizontal) and the photon is not altered.
However, if the photon is vibrating in an intermediate direction (for example at 45º), this can happen if it is in a superposition of the two reference directions at the same time (horizontal and vertical at the same time), when measuring polarization We will obtain one of the two values at random (for example 50% vertical / 50% horizontal) and the photon will undergo an alteration and will be forced to change to the direction we have measured.
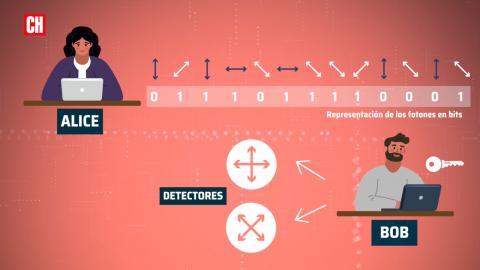
Once quantum key distribution is explained, let’s imagine a chain of communication between the two most popular characters in computing: Bob and Alice. Alice is the sender of the encrypted message and Bob the receiver, it is necessary that both share a key to know how to decrypt the initial message.
To share the key with Bob, Alice gives a bit to each polarized photon that she will send to Bob (0 = Horizontal; 1 = Vertical and 0 = -45º; 1 = + 45º). Photons polarized in four different directions are sent out completely randomly. On the other side, there is Bob who is the legitimate recipient of that key and who has two different detectors to measure those photons that Alice sends him. One detector measures vertical and horizontal photons and the second detector can only measure photons in the other two directions at + 45º and -45º.

Bob is also going to use these detectors randomly so he has a 50% chance of measuring the photons that Alice sends with the corresponding detector. When he finishes measuring Alice’s message, Bob tells her about the random sequence of detectors he has used and Alice compares it to his sequence and tells her where he has used the wrong detector.
So Bob knows which part of Alice’s sequence he has registered correctly and which could have given random errors and he must discard it, out of 1,000 photons we have 500 left. The encrypted message, as well as the sequence of detectors used by Bob are shared in a traditional way (easier to spy), as we do now, but the key in photon format is no longer so easy to intercept.
If an intruder tries to listen to the sequence of photons that Alice is sending to Bob, by measuring the photons along the way, he is also disturbing his quantum state and what reaches Bob is no longer the same as Alice sent. How do they know that there is an intruder that has caused errors in the photon chain? Because Bob chooses a piece of the bit sequence that he has resulted from measuring Alice’s photons (with the correct detectors) and sends it to her. If Alice sees that even having used the detectors in the correct order, Bob has wrong bits in that small part, she sounds the alarm, because something is disturbing the photons along the way.
If they do not find errors, Alice approves that piece, so that Bob knows that they are on the right track and the remaining part in bits that have not been shared by any channel must also be correct, that is the definitive key to decrypt the information that you want to transmit.
The transmission of single photons through an optical fiber is very sensitive to errors. Even without the action of a hacker, a photon can be altered by interaction with an external radiation or an atom in the fiber, this causes additional errors. To correct these errors Alice and Bob use a correction algorithm that is already used in traditional communication systems or in NAS storage redundancy systems. This further reduces the final length of the validated and corrected key.
After all these verification processes, the final key is a small part of the original sequence that Alice issued. For added security, this entire process between Alice and Bob is repeated every few seconds, renewing the encryption keys and greatly reducing the chances of a hack.
This is what is known as quantum key distribution, a very new technology that is struggling to reach greater transmission distances, since the emission of photons is something very sensitive that can suffer many alterations along the way even if there is no one spying. The products that are already being marketed reach tens or hundreds of kilometers. To lengthen these distances, we are resorting to repetition nodes, which do the same function as Alice and Bob, over and over again, and which you can see in this network built in China.
Another problem of quantum key distribution technology that is being solved is the security of these intermediate nodes. If they are hacked, in them the key is not protected by the quantum system and they would be easier points to attack on the network. As a solution, quantum teleportation is being studied, the development of quantum repeaters in which the key is transmitted and quantum validated from end to end. But we will talk about this another day.