The integrated TPM chips (Trusted Module Platform) are, today, a key element in the security of systems. So much so that, as you may well know, Microsoft will only allow the installation of Windows 11 on systems equipped with this security system (with some exceptions, as we already told you here ), putting users of old systems that do not have it in a difficult situation. with TPM chip and they don’t have the possibility to install it either.
And it is that the commitment of manufacturers and developers for the chips dedicated to guaranteeing the security of certain operations is more than decided, with TPM accompanying compatible systems and a secure enclave such as their implementation designed by Apple. And there is no doubt that in the vast majority of cases, this system offers a more than adequate level of security and with which we can remain calm.
However, TPM has turned out not to be infallible, in certain circumstances and with a complex but feasible procedure, it is possible to bypass the protection that in theory prevents powering up and using a system and, in the same circumstances, accessing a corporate network, with the enormous risks this poses. Before going into analyzing the vulnerability, I reiterate what I mentioned before, they are very specific circumstances, and it is not an attack available to everyone, but it is still important to know it and, if necessary, prevent it.
This discovery is the result of an investigation carried out and made public a few days ago by Dolos Group, and whose authors achieved full access to the hard drive of a laptop preconfigured to offer access to a corporate network through a secure VPN connection. This type of preconfiguration is very common in companies that deliver this equipment to their workers so that they can telework safely.
TPM is safe, its implementation not so much…
Given the security offered by the TPM chip, many attacks are ruled out, so the researchers tried a different approach, that is, they looked for weaknesses related to the chip itself and its integration into the system. With the most common configuration, when the system starts up Windows directly, without a previous step in which it is necessary to enter a password. A single key, stored on the chip, with which the system is unlocked.
The construction of the TPM chips themselves makes attempting to directly access their content virtually impossible. It is even claimed that there are some models with a physical self-destruct function in case of detecting attempts to access their interior. For its part, the points that join the chip to the board are so small that, in practice, it is almost impossible to solder something to them to try to access the data that is transmitted to and from the integrated.
And what is the use of accessing such data traffic? This is when we have to know that the connection from the TPM to the CPU is made through an SPI bus (Serial Peripheral Interface) and that, due to BitLocker’s security implementation, placing a sniffer on that data bus could allow us to get hold of the decryption key from the system storage drive, as it is transmitted unencrypted.
Ideally, for safety reasons, the TPM would have an exclusive bus that connects it to the CPU, but for design and cost reasons, it turns out that the same bus used in this connection is also used by other components on the board. base, including the CMOS chip that houses the system BIOS. And what is unique about this chip? Well, unlike the TPM, the pins that connect it to the motherboard are large, so connecting something to them is much easier.
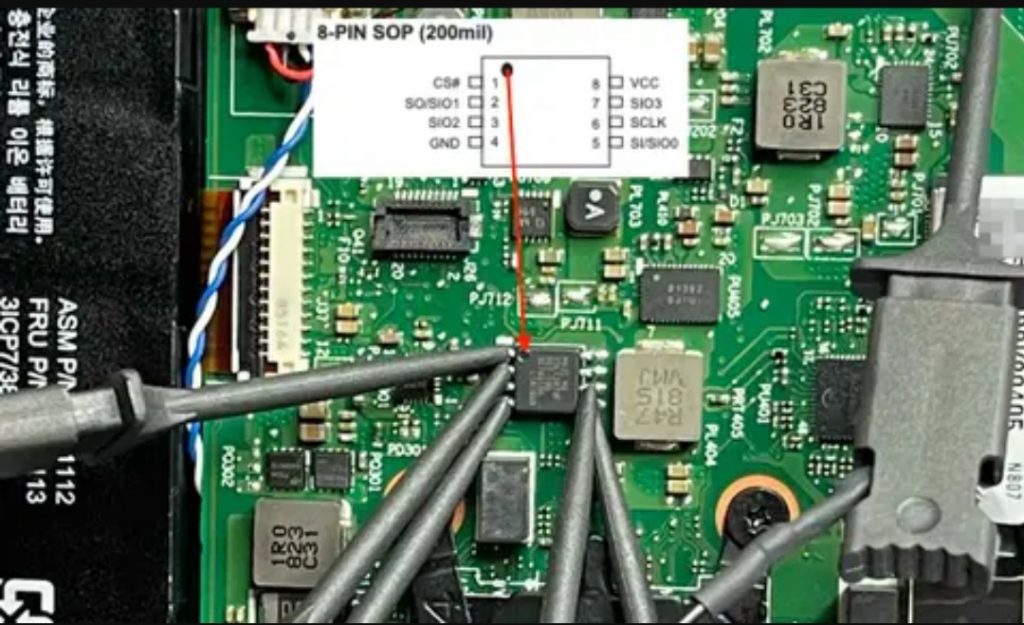
The next step was to analyze all the data traffic on the SPI bus to which both the BIOS and the TPM chip were connected , filtering all the data to extract the encryption key. It didn’t take them too long to take advantage of the system accesses to the hard drive to gain access to the contents of the storage drive. From that very moment, the war was already won, the researchers had already obtained the necessary key to decipher the contents of the disc.
With the drive decryption key obtained, researchers no longer had to face the impossibility of unlocking the system without the key: the next step was to disconnect the SSD from the laptop and connect it to another system to access its contents.
Even worse than it seemed
During the analysis of the contents of the hard disk, a most interesting finding was made: the PC had a corporate VPN client installed, pre-installed and preconfigured, ready to use. Unlike VPN clients for home users, business solutions have a very interesting feature: they establish the connection before the user logs in. In this way, the domain scripts are executed on the systems as soon as they are turned on, avoiding the need for password authentication (specific to each computer) in each case, something that could be a nightmare for the administrator of said systems.
What does this mean? Well, at that point, researchers, and potential attackers, could resort to many techniques, well known, to introduce malware into the SSD of the attacked system, which would later be mounted again on the PC. And when that PC, or a dump of its disk in a virtual machine, starts up, it will immediately access the corporate network, so not only the security of that system will have been compromised, but the entire infrastructure.
As I indicated at the beginning, we are talking about a complex attack, since it requires physical access to the system and, with certain additional security measures, it is invalidated. The simplest option is that the user must enter a password to start the system (the system itself, not Windows), and an additional security system can also be used that makes the communications between the TPM and the CPU yes that are encrypted.
We are talking, therefore, about a security problem that is not easy to exploit, but that exists, that can be reproduced (more now, that has been made public) and that shows that even having a TPM chip does not guarantee complete security. And as a result, it is essential to take additional measures, such as blocking the system startup with a password.
And there is one recommendation that is key, above all others: remember that we will never have 100% security. We already have a TPM chip, a very secure VPN, etc., we must not neglect security. Keep our computers under surveillance, do not install software of dubious origins, be very careful with what we receive by email… yes, I know, they are the same guidelines as always, but their importance is fundamental when it comes to protecting ourselves from threats.